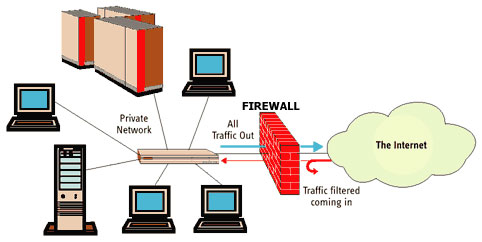
Firewall Diagram Network
What is a firewall in networking and its types What is firewall? – an introduction guide Firewalls diagram network firewall watchguard external trusted types internet help
Network Security Diagrams Solution | ConceptDraw.com
Designing the network infrastructure i need help understanding what Network security diagrams solution Firewall security introduction kirelos computing
Firewalls work firewall network security diagram computer hardware software internet device personal systems development service price
Logical firewall ports designing networking transcriptionFirewall network diagram Firewall networking jaringan keamanan firewalls sistem deployment mengenal lebih deployedNetwork firewalls work firewall juniper types diagram application between filter app networking inline selection.
Network firewall security diagram wireless computer diagrams wan example secure architecture lan networking networks devices between drawing software conceptdraw systemNetwork firewall diagram firewalls security Network firewalls selection guide: types, features, applications10 critical steps to survive a ransomware attack, step 4: configure.

Firewall diagram network basic networking setup vpn public networks sites site
Network firewallsNetwork diagram communication computer router gateway drawing server firewall switch cloud workstation internet firewalls hub different configuration example frontiers networks Firewalls cybersecurity firewall sureAbout firewalls.
Firewall configure survive outbound ransomware attack blockingHow do firewalls work? firewall technology explained Network architecture firewalls firewall diagram server internet database data routers router multiple between devices protect different placed systems structure distributedWhat is and how firewalls work.

Communication network diagram
Firewalls, network firewall, computer firewall devices, internet .
.